Top 5 Best Practices for Secure Data Destruction & Disposal
 7
7 Aug
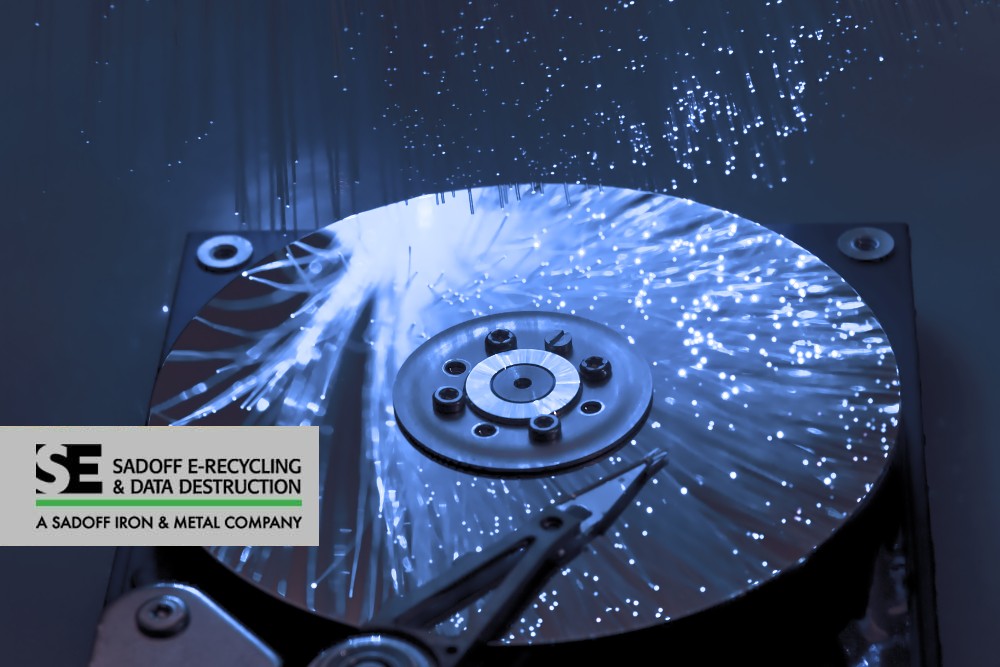
In today’s digital age, businesses of all sizes collect and store vast amounts of sensitive data. This data includes customer information, employee records, financial data, and intellectual property. When it’s time to dispose of old computers, hard drives, or other data-bearing devices, simply deleting files or formatting drives is not enough to ensure the complete erasure of this information.
Read More: Is Formatting a Hard Drive Good Enough For Data Security
Best Practices for Data Security
To protect your business from the risks of data breaches and ensure compliance with privacy regulations, it’s crucial to partner with a professional data destruction service. But what are the best practices for secure data destruction and disposal?
1. Develop a Documented Process
The first step to secure data destruction is to develop a documented process that outlines how sensitive data will be destroyed. This process should include:
- The types of data that need to be destroyed
- The methods of destruction that will be used
- The frequency of destruction
- The disposal of destroyed data
Creating a documented process for data destruction ensures consistency and accountability within your organization. This process should clearly define the types of data that require destruction, the approved destruction methods (such as physical shredding, degaussing, or software-based wiping), and the frequency with which destruction should occur.
It should also detail the procedures for securely disposing of destroyed data and maintaining records of the destruction process. If you’re unsure where to start, consulting with a data destruction expert like Sadoff can help you develop a comprehensive and compliant plan tailored to your specific needs and industry regulations.
What is an ITAD Program and Why Do You Need One?
2. Create a Records Retention Schedule
A records retention schedule is a crucial component of data management and compliance. It outlines how long different types of data should be retained based on legal, regulatory, and business requirements. Having a well-defined schedule helps you avoid unnecessary data storage, reducing the risk of data breaches and ensuring compliance with industry-specific regulations.
Collaborating with legal and compliance experts can ensure your schedule aligns with your specific business needs. This schedule should clearly identify the types of data your organization handles, the minimum and maximum retention periods for each type, and the secure destruction procedures to follow once data reaches its end-of-life.
3. Use a Variety of Data Destruction Methods
Effective data destruction relies on proven methods that ensure data is irretrievably erased. Some of the most reliable techniques include:
 Degaussing—This process uses a powerful magnetic field to disrupt the magnetic patterns on hard drives and other magnetic media, rendering data unrecoverable.
Degaussing—This process uses a powerful magnetic field to disrupt the magnetic patterns on hard drives and other magnetic media, rendering data unrecoverable.- Physical Destruction—This involves physically destroying the storage media, rendering it unusable and preventing any access to the data. Common methods include shredding, crushing, and disintegrating.
- Overwriting—Specialized software overwrites data on storage devices multiple times with random patterns, making the original data unrecoverable even with advanced forensic tools. Ensure the overwriting software adheres to recognized standards like those set by the Department of Defense (DoD).
Read More: Learn More About the Methods of Data Destruction Available
Remember, the choice of data destruction method depends on the type of media, sensitivity of the data, and any industry-specific regulations. A reputable data destruction service like Sadoff can help you determine the most appropriate approach for your needs.
4. Track and Document the Destruction Process
Maintaining a thorough and auditable record of data destruction is crucial for compliance and accountability. Each data-bearing device should have a documented history that includes:
- Device Identification—Clearly record the type of device (hard drive, SSD, tape, etc.) and its unique identifier (serial number, asset tag).
- Destruction Details—Document the date and time of destruction, the method used, and any relevant details specific to the destruction process.
- Chain of Custody—Maintain a clear record of who handled the device at each stage of the destruction process, ensuring accountability and preventing unauthorized access to the data.
Certified data destruction services like those offered by Sadoff provide detailed reports and certificates of destruction, serving as official proof that your data has been handled securely and in compliance with industry regulations.
5. Partner with a reputable data destruction service.
A reputable data destruction service will have the expertise and experience to securely destroy your data in accordance with industry standards. They will also be able to provide you with documentation of the destruction process.
Data destruction isn’t merely a final act; it’s an integral part of a responsible lifecycle for your IT assets. Whether your business is in healthcare, finance, or any other sector handling sensitive information, partnering with a certified expert ensures compliance and safeguards your reputation.
Beyond Destruction: A Sustainable Partnership
Sadoff E-Recycling and Data Destruction offers comprehensive solutions to protect your data, going beyond simple destruction. We provide certified data erasure services, meticulous documentation, and environmentally responsible recycling of your electronic waste. And, when combined with SunCoast Communications’ expertise in asset recovery and resale, your outdated telecom and data center equipment can find new life, further reducing environmental impact and maximizing value.
Secure data destruction is not just a legal necessity. It’s a commitment to ethical business practices and environmental stewardship. Contact Sadoff or SunCoast today to explore how we can tailor a solution to your specific needs, ensuring your data is protected and your equipment handled responsibly.
Categorized in: Data Security




 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions