CATEGORY: Data Security
 8
8
Jul
In the story of business risks, we always cast phishing and malware as the main villains. But there is another threat we often forget about. The physical hardware that stores our most important information. That single old server in the... View Article
 13
13
Sep
In today’s digital age, data is the lifeblood of most businesses. However, data also represents a significant vulnerability. When data reaches the end of its lifecycle or when hardware is decommissioned, it’s crucial to ensure that sensitive information is completely... View Article
 7
7
Aug
In today’s digital age, businesses of all sizes collect and store vast amounts of sensitive data. This data includes customer information, employee records, financial data, and intellectual property. When it’s time to dispose of old computers, hard drives, or other... View Article
 5
5
Jul
In today’s digital age, businesses across all industries collect and store vast amounts of sensitive data. This includes customer information, employee records, financial data, and intellectual property. When it’s time to dispose of old computers, hard drives, or other data-bearing... View Article
 12
12
Jun
In today’s digital landscape, our lives are intertwined with electronic devices. From personal smartphones and laptops to business servers and medical equipment, these devices store a wealth of sensitive information. When these electronics reach the end of their lifespan, the... View Article
 21
21
Mar
Data centers are the backbone of the digital economy. But as technology evolves, data centers can become outdated, inefficient, or even obsolete. While the decision to decommission a data center is undoubtedly complex, it can yield numerous benefits ranging from... View Article
 21
21
Feb
The saying “once on the internet, always on the internet” highlights an important truth—data has a way of sticking around. This principle also applies to our physical devices. Simply hitting “delete” on your old computer, phone, or hard drive does... View Article
 20
20
Feb
In today’s digital world, our computers hold an incredible amount of personal information. From financial records and login credentials to customer databases and confidential business documents, your old computer has the potential to become a treasure trove for prying eyes.... View Article
 19
19
Feb
Did you know that most of your computer can be recycled? From the metal casing to circuit boards and even some plastics, valuable resources can be recovered, preventing them from ending up in landfills. However, when it comes to safely... View Article
 13
13
Feb
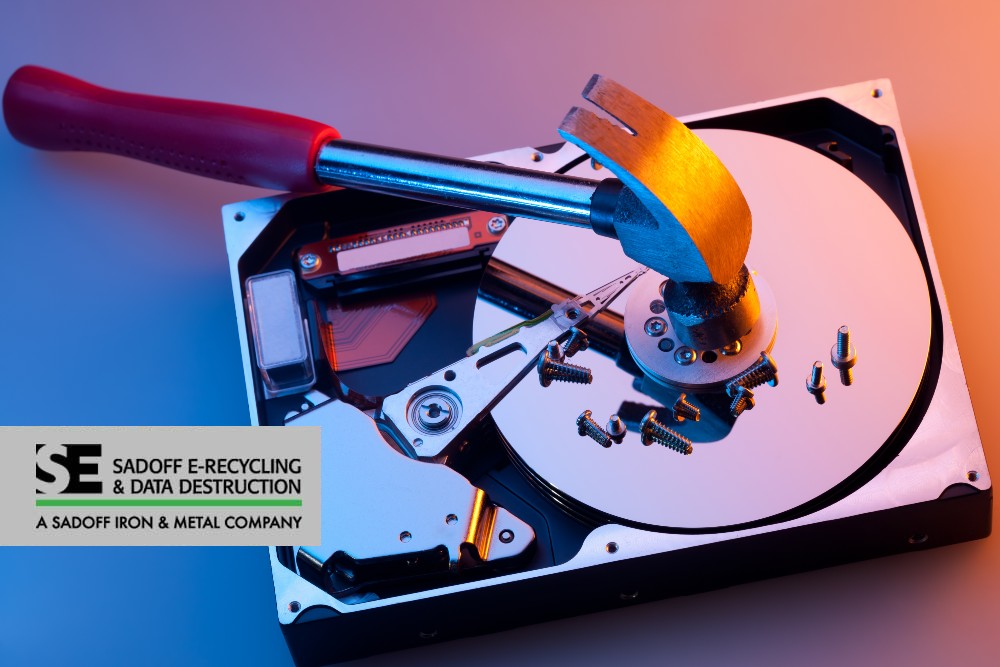
You have seen images and videos of people taking their hard drive destruction into their own hands. They bring out powerful magnets, use power tools, and often even resort to a hammer. Can you physically destroy a hard drive yourself?... View Article
 8
8 








 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions
 Google map directions
Google map directions